安装cert-manager
helm repo add jetstack https://charts.jetstack.io helm install \ --name-template cert-manager \ --namespace kube-public \ --set image.repository=registry.cn-shanghai.aliyuncs.com/wanfei/cert-manager-controller \ --set ingressShim.defaultIssuerName=letsencrypt-prod \ --set ingressShim.defaultIssuerKind=ClusterIssuer \ --version v0.12.0 \ jetstack/cert-manager
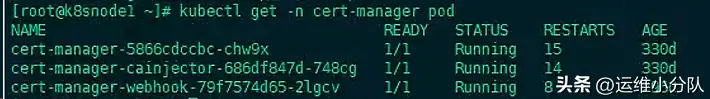
查看Pod状态
kubectl get pods --namespace kube-public -o wide
创建ClusterIssuer 测试cert-manager
cat <<EOF > test-resources.yaml
apiVersion: v1
kind: Namespace
metadata:
name: cert-manager-test
---
apiVersion: cert-manager.io/v1alpha2
kind: Issuer
metadata:
name: test-selfsigned
namespace: cert-manager-test
spec:
selfSigned: {}
---
apiVersion: cert-manager.io/v1alpha2
kind: Certificate
metadata:
name: selfsigned-cert
namespace: cert-manager-test
spec:
commonName: example.com
secretName: selfsigned-cert-tls
issuerRef:
name: test-selfsigned
EOF
创建测试资源
[root@i-35l7b2rr ~]# kubectl describe certificate.cert-manager.io -n cert-manager-test
Name: selfsigned-cert
Namespace: cert-manager-test
Labels: <none>
Annotations: <none>
API Version: cert-manager.io/v1alpha2
Kind: Certificate
Metadata:
Creation Timestamp: 2021-07-08T01:45:20Z
Generation: 1
Managed Fields:
API Version: cert-manager.io/v1alpha2
Fields Type: FieldsV1
fieldsV1:
f:status:
.:
f:conditions:
f:notAfter:
Manager: controller
Operation: Update
Time: 2021-07-08T01:45:20Z
API Version: cert-manager.io/v1alpha2
Fields Type: FieldsV1
fieldsV1:
f:metadata:
f:annotations:
.:
f:kubectl.kubernetes.io/last-applied-configuration:
f:spec:
.:
f:commonName:
f:issuerRef:
.:
f:name:
f:secretName:
Manager: kubectl-client-side-apply
Operation: Update
Time: 2021-07-08T01:45:20Z
Resource Version: 1688874
UID: 682ffb9c-4594-4404-8d0d-61d0b9fdb03a
Spec:
Common Name: example.com
Issuer Ref:
Name: test-selfsigned
Secret Name: selfsigned-cert-tls
Status:
Conditions:
Last Transition Time: 2021-07-08T01:45:20Z
Message: Certificate is up to date and has not expired
Reason: Ready
Status: True
Type: Ready
Not After: 2021-10-06T01:45:20Z
Events:
Type Reason Age From Message
---- ------ ---- ---- -------
Normal GeneratedKey 21s cert-manager Generated a new private key ### this
Normal Requested 21s cert-manager Created new CertificateRequest resource "selfsigned-cert-2334779822" ### this
Normal Issued 21s cert-manager Certificate issued successfully
清理测试资源
kubectl delete -f test-resources.yaml
创建签发机构
cat <<EOF> production-issuer.yaml
apiVersion: cert-manager.io/v1alpha2
kind: ClusterIssuer
metadata:
name: letsencrypt-prod
spec:
acme:
# The ACME server URL
server: https://acme-v02.api.letsencrypt.org/directory
# Email address used for ACME registration
email: abc@abc.com
# Name of a secret used to store the ACME account private key
privateKeySecretRef:
name: letsencrypt-prod
# Enable the HTTP-01 challenge provider
solvers:
- http01:
ingress:
class: nginx
EOF
. metadata.name 是我们创建的签发机构的名称,后面我们创建证书的时候会引用它
. spec.acme.email 是你自己的邮箱,证书快过期的时候会有邮件提醒,不过 cert-manager 会利用 acme 协议自动给我们重新颁发证书来续期
. spec.acme.server 是 acme 协议的服务端,我们这里用 Let’s Encrypt,这个地址就写死成这样就行
. spec.acme.privateKeySecretRef 指示此签发机构的私钥将要存储到哪个 Secret 对象中,名称不重要
. spec.acme.http01 这里指示签发机构使用 HTTP-01 的方式进行 acme 协议 (还可以用 DNS 方式,acme 协议的目的是证明这台机器和域名都是属于你的,然后才准许给你颁发证书)
Ingress 配置(添加注解)
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
annotations:
# add an annotation indicating the issuer to use.
cert-manager.io/cluster-issuer: nameOfClusterIssuer
name: myIngress
namespace: myIngress
spec:
rules:
- host: example.com
http:
paths:
- pathType: Prefix
path: /
backend:
service:
name: myservice
port:
number: 80
tls: # < placing a host in the TLS config will determine what ends up in the cert's subjectAltNames
- hosts:
- example.com
secretName: myingress-cert # < cert-manager will store the created certificate in this secret.
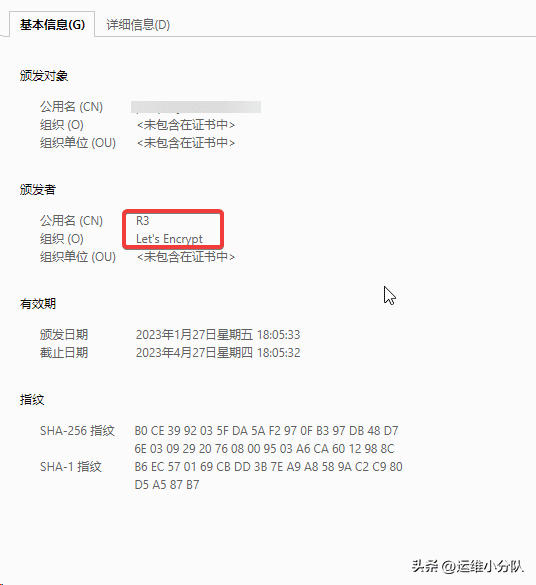
到期后cert-manger会自动续期。每次续期3个月
转载作品,原作者:运维小分队,文章来源:https://www.toutiao.com/article/7214386591199363645

 微信赞赏
微信赞赏  支付宝赞赏
支付宝赞赏